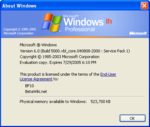
Windows Vista build 5000 (vbl_core.040808-2000)
| Build of Windows Vista | |
 | |
| OS family | Windows NT |
|---|---|
| Version number | 6.0 |
| Build number | 5000 |
| Architecture | x86 |
| Build lab | vbl_core |
| Compiled on | 2004-08-08 |
| Expiration date | |
| Timebomb | 2005-08-03 (+360 days) |
| SKUs | |
| Professional | |
| Product key | |
| TCP8W-T8PQJ-WWRRH-QH76C-99FBW | |
| About dialog | |
Windows Vista build 5000 (vbl_core.040808-2000) is a build of Windows Vista. On 23 January 2020, this build was listed on a thread by UX.Unleaked blog founder Grabberslasher to be released to the BetaArchive FTP, and was released in the third set of his 33 Longhorn/Vista builds on 26 January 2020, alongside build 4048, other compiles of this build, and build 5001.[1]
This build by default has a severe bug where it appears to hang as soon as Windows switches to graphical mode, ending up with a solid blue or black screen, making this build not installable under normal conditions.
Bug analysis[edit | edit source]
Module name: win32k.sys
Reason: An uninitialised variable which causes win32k to raise Access Violation exception (by reading null pointer) and failing without any notice.
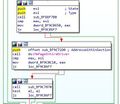
When Windows loads, it only shows a blank blue or black background without any cursor or watermark. Keyboard interrupts are also stuck/unregistered. First checks show that kernel idle loop is running fine and processing interrupts. There are no exceptions or bugchecks logged into WinDbg, hence the next check is to set breakpoints on nt!ExRaiseStatus and nt!ExRaiseAccessViolation, which apparently is what win32k is calling and leaving the function it is in. According to the following stack, it is either being called at win32k!EngFreeModule+0x5c9 (the preceding instruction), or the called function has called it:
f75d6d24 nt!ExRaiseAccessViolation f75d6d48 win32k!EngFreeModule+0x5ce f75d6d50 win32k!EngFreeModule+0x4b5 f75d6da0 nt!KeReleaseInStackQueuedSpinLockFromDpcLevel+0xb14 f75d6da4 ntdll+0x18c3c f75d6da8 0x75a69626
Checking the code, it is calling the function located at win32k!EngMulDiv+0x29c0:
win32k!EngFreeModule+0x5b1: bf8a0581 e84a5effff call win32k!EngMultiByteToUnicodeN+0x4310 (bf8963d0) bf8a0586 893530079cbf mov dword ptr [win32k!HT_Get8BPPMaskPalette+0x30bb0 (bf9c0730)],esi bf8a058c 8935cc219cbf mov dword ptr [win32k!HT_Get8BPPMaskPalette+0x3264c (bf9c21cc)],esi bf8a0592 ff1500119abf call dword ptr [win32k!HT_Get8BPPMaskPalette+0x11580 (bf9a1100)] bf8a0598 50 push eax bf8a0599 e8e280f8ff call win32k!EngMulDiv+0x29c0 (bf828680) bf8a059e 8bd8 mov ebx,eax <-- The return address in the stack, second frame (win32k!EngFreeModule+0x5ce) bf8a05a0 3bdf cmp ebx,edi
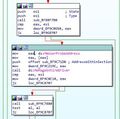
Inside that procedure, using a line-by-line tracing where it ends up calling ExRaiseAccessViolation has been found in the following part:
win32k!EngMulDiv+0x2b62:
=== bf828822 3b0d9c219cbf cmp ecx,dword ptr [win32k!HT_Get8BPPMaskPalette+0x3261c (bf9c219c)] ds:0023:bf9c219c=00000000 ===
win32k!EngMulDiv+0x2b68:
bf828828 0f8721fcffff ja win32k!EngMulDiv+0x278f (bf82844f) [br=1]
win32k!EngMulDiv+0x278f:
bf82844f ff1580109abf call dword ptr [win32k!HT_Get8BPPMaskPalette+0x11500 (bf9a1080)] ds:0023:bf9a1080={nt!ExRaiseAccessViolation (809849aa)}
Comparing it with build 5000 (vbl_core.040809-2000)'s win32k.sys, the content of win32k!HT_Get8BPPMaskPalette+0x3261c (bf9c219c) in this build's win32k.sys is 7fff0000 instead of 00000000. At this point, the location of the failure has been pinpointed. With some additional comparison against build 5000 (vbl_core.040808-2000)'s win32k.sys, where that address is being filled up has been found:
Build 5000 (vbl_core.040809-2000)
win32k.sys
Workarounds[edit | edit source]
- Replace
win32k.syswith build 5000 (vbl_core.040809-2000)'s, as comparing it against this build'swin32k.systurns up this only change and it will operate just as it was patched. - By using WinDbg: once breaking into the session, type:
ba e1 bf9c73b3 "r eax=7fff0000;e bf9c219c 00 00 ff 7f;gc"
- It will now adjust the content of that address and continue.
Bugs and quirks[edit | edit source]
Windows Explorer[edit | edit source]
The details pane in Windows Explorer does not function correctly, while panes and tasks that work cannot be opened or closed. In the Control Panel, they also quickly dissapear after loading, making it almost impossible to switch to Classic View. This issue can be resolved by disabling the "Fade or slide menus into view" option in the Performance Options.
Out-of-box experience[edit | edit source]
The animated "Question Mark" assistant in the Out-of-box experience does not appear until the second page of OOBE is reached, which may be due to bugs in the Microsoft Agent technology itself.
Windows Media Player[edit | edit source]
The visualizations in Windows Media Player do not function correctly.