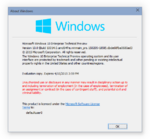
Windows 10 build 10014 (winmain_prs)
| Build of Windows 10 | |
 | |
| OS family | Windows NT |
|---|---|
| Version number | 10.0 |
| Build number | 10014 |
| Build revision | 0 |
| Architecture | x86, x64 |
| Build lab | winmain_prs |
| Compiled on | 2015-02-05 |
| Expiration date | |
| Timebomb | 2015-04-15 (+69 days) |
| About dialog | |
Windows 10 build 10014 (winmain_prs) is a build of Windows 10, which was shared online on BetaArchive on 23 March 2015 in the form of a modded copy.[1] The unmodified copy of this build was later uploaded to BetaArchive on 8 May 2016. Prior to it being shared, several screenshots of this build were shown in a tweet on 22 February 2015.[2]
It is the earliest available build to contain the Education SKU, which is accessible by upgrading from the Pro SKU.
Editions and keys[edit | edit source]
| Edition / SKU Name | Key |
|---|---|
| Core | 334NH-RXG76-64THK-C7CKG-D3VPT |
| Professional | NKJFK-GPHP7-G8C3J-P6JXR-HQRJR |
| ProfessionalWMC (edition upgrade only) | GBFNG-2X3TC-8R27F-RMKYB-JK7QT |
| Enterprise | PBHCJ-Q2NYD-2PX34-T2TD6-233PK |
| Education (edition upgrade only) | NCQDD-DCDRV-HRG6J-4F7PF-TVJDF |
Bugs and quirks[edit | edit source]
Administrator privileges[edit | edit source]
The first local user account created during installation of this build would not be placed in the local Administrators group, which prevents any operations that need to be performed with elevated privileges. It can be resolved by booting Windows in safe mode, and changing group membership for the local user account using the Local Users and Groups tool (lusrmgr.msc) in Computer Management.