Windows Server 2019 build 17623
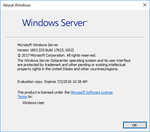
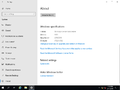
| Build of Windows Server 2019 | |
 | |
| OS family | Windows 10 (NT 10.0) |
|---|---|
| Version number | 10.0 |
| Build number | 17623 |
| Build revision | 1002 |
| Architecture | x64 |
| Build lab | rs_prerelease |
| Compiled on | 2018-03-10 |
| Expiration date | |
| Timebomb | 2018-07-02 (+114 days) |
| SKUs | |
| Standard Server Standard Server Core Datacenter Server Datacenter Server Core | |
| About dialog | |
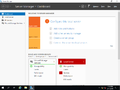
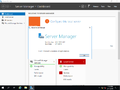
Windows Server 2019 build 17623 is the first Insider Preview build of Windows Server 2019. It was released on 20 March 2018. It is notably the first Windows Server Insider build to have the ability to boot on the current date.
New features and changes[edit | edit source]
- Users can extend their cluster systems with Cluster Sets. This feature is a new cloud-based scale-out technology. It increases the cluster node count in a single SDDC (Software-Defined Data Center) based cloud by orders of magnitude. A Cluster Set is a loosely-coupled group of multiple failover clusters of the three types, compute, storage and hyper-converged. It enables virtual machine fluidity across clusters that are members of the Cluster Set, plus a unified storage namespace across the network with the Cluster Sets that utilizes virtual machine fluidity.
- Windows Defender Advanced Threat Protection now provides deep platform sensors and quicker responses to memory and kernel attack activities and abilities to take actions on affected machines. These can be in response to such incidents such as remote collection of additional forensic data, remediating malicious files and terminating malicious processes, and other such activities.
- Introduced Windows Defender ATP Exploit Guard. It is a set of host intrusion prevention capabilities, divided into four components. The first of these components are Attack Surface Reduction, which is a set of controls that enterprises can use to block malware from getting onto the machine by blocking questionable files, the second being Network Protection, which protects an endpoint against web-based threats by blocking any outbound process on the device to untrusted hosts and IPs by using Windows Defender SmartScreen, the third is controlled folder access, which protects data from ransomware by blocking suspicious processes from accessing the user's protected folders, and the fourth being exploit protection, which is a set of vulnerability exploit mitigations that can be configured to protect the system and applications.
- Failover Clusters no longer use the legacy NTLM authentication. It uses Kerberos and certificate based authentication instead.
- Shielded virtual machines can now run on Hyper-V hosts that suffer intermittent connectivity to their Host Guardian Service (HGS). The new feature, Fallback HGS allows the user to configure a second set of URLs for the hypervisor to try if it can't reach the primary HGS server. Offline mode was also introduced to allow the user to start up a shielded VM even if the host's primary and fallback HGSs can't be reached, under one of the following scenarios: as long as the VM has been successfully started at least once on that host and the host's security configuration has not been changed since then. To enable offline mode, run the following PowerShell cmdlet on the Host Guardian Service:
Set-HgsKeyProtectionConfiguration –AllowKeyMaterialCaching. - Made it easier to troubleshoot shielded VMs by enabling support for VMConnect Enhanced Session Mode and PowerShell Direct.
- You can now run Ubuntu, Red Hat Enterprise Linux, and SUSE Linux Enterprise Server inside shielded virtual machines.
- This is, as of today, the only build of Windows Server 2019 to use a 2017 copyright date in
winver.exe, as the next build already uses a 2018 copyright date. - Add a new feature named "Encrypted Networks". It provides a simple to configure DTLS-based encryption using the network controller to manage the end-to-end encryption and protect data as it travels through the connection between the hosts. It is configured by sysadmins on a per-subnet basis. It enables the VM to VM traffic within a VM subnet to be automatically encrypted as it leaves the host.
Bugs[edit | edit source]
- Active Directory domain controllers may not upgrade correctly during an in-place OS upgrade.
- If you create or edit a policy for AppLocker, the associated MMC snap-in can crash when generated rules for a packaged app.
- After an upgrade, the AppX database may have corrupted entries, which can cause problems for components that use said entries.
- If you test the Windows core, it may fail because of a timeout while attempting to load the test libraries.
SKUs and keys[edit | edit source]
| Edition / SKU Name | Key |
|---|---|
| Standard Server | MFY9F-XBN2F-TYFMP-CCV49-RMYVH |
| Datacenter Server | 6XBNX-4JQGW-QX6QG-74P76-72V67 |
Gallery[edit | edit source]
Settings app